Detecting the Hidden Signatures of Illicit Activity
STR’s graph analytics tools align entities across disparate data sources and efficiently perform example-based search to rapidly detect potential illicit activity.
Operating human smuggling rings, developing weapons of mass destruction, and running criminal enterprises involve acquiring materials, recruiting actors, moving funds, and coordinating complex operations. Despite efforts to obscure these activities, the resulting transactions leave a faint but observable signature that is hidden in vast quantities of normal commerce, communication, and financial transaction data. However, the significance of an event in one data source may only become apparent when placed in the context of the actor’s other activities.
To address these challenges, DARPA selected STR to provide technology for an initiative called Modeling Adversarial Activities (MAA) that sought to extend capabilities for detecting adversarial activities by finding subtle indicators and warnings in the data, particularly when the data come from unaligned, heterogeneous data sources. To address this goal, STR has developed a graph merging technology called hierarchical entity alignment technologies (HEAT) and activity detection capabilities called warnings of activities via efficient subgraph-matching (WAVES). The two technologies can be run either separately or sequentially.
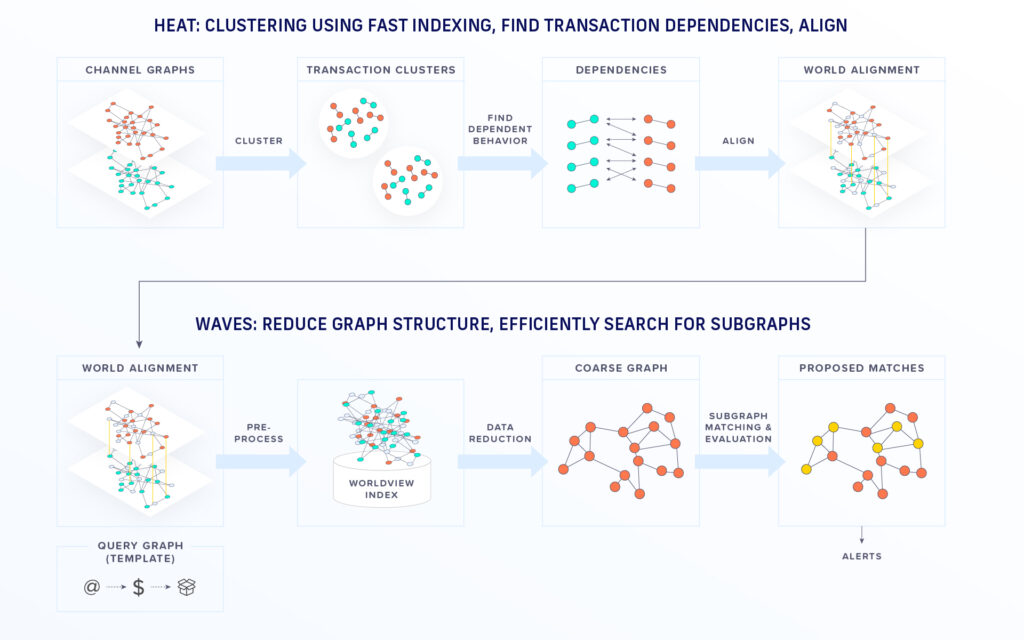
STR’s HEAT generates a unified representation of the connections between people, organizations, places and other entities. HEAT aligns these entities across disparate data sources using both inherent and contextual information. Our HEAT system is based on a Bayesian probabilistic model that takes in sample knowledge graphs and uses them to estimate the joint distribution of the graphs. The algorithm estimates the probabilities of the classes or property values of an unknown node or edge, The aligned entities from HEAT are collapsed into single entities, resulting in a merged world view background graph to provide a more accurate basis for activity detection.
Heat generates a representation of the tangled connections between people, organizations, places and their activities
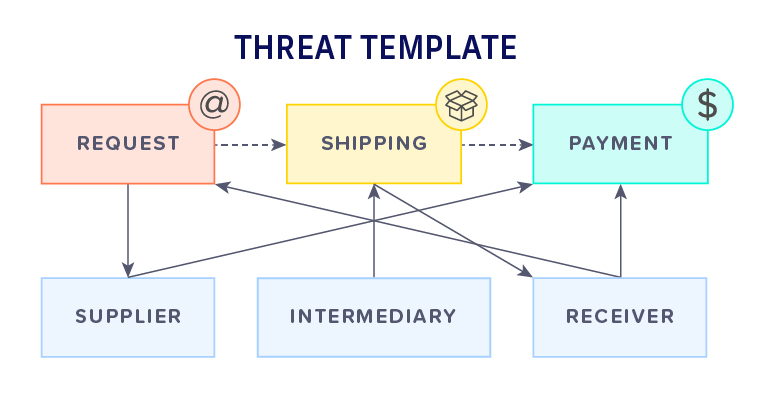
Meanwhile, the companion tool WAVES uses known patterns of illicit activity and seeks out these patterns in the merged worldview graph. The template is represented as a small graph and can have arbitrary complexity. A simple example of materials acquisition is illustrated here including communication, shipping and financial data sources. WAVES produces as output the top-ranked distinct subgraphs that best match the threat template, including inexact matches if needed. WAVES first performs efficient data reduction to quickly focus on the sections of the worldview graph of interest. The system then employs an efficient subgraph matching algorithm to rapidly detect potential threat templates in the worldview graph.
Over the past several years STR has applied our HEAT+WAVES technology to use cases ranging from illicit weapons procurement to human smuggling, developing a system that can process graphs of millions of nodes and edges in just a few minutes on modern computing environments. STR is currently transitioning HEAT + WAVES to select government agencies while looking for additional partners who could benefit from the capability. Our team welcomes the opportunity to demonstrate this system and explore operationalization. Please contact us at MAA@str.us.
Distribution Statement A: Approved for Public Release, Distribution Unlimited
Further reading:
Douglas et al. (2018) “Metrics for Evaluating Network Alignment”. GTA3, February 2018.
Franklin Abodo, Philip Marvin, Joanna Brown. (2022) “Graph Reachability Pruning: Adaptive Data Reduction for Inexact Subgraph Matching”. Submitted to SIGIR ’22.